Table of contents
Data anonymization: The pillar of ethical web analytics
Sep 14, 2023
8 mins read
Written by Usermaven

According to the DBTA Report on meeting the growing challenges of data security & governance, there has been a staggering 70% rise in data compromises from 2020 to 2021. The impact of each data breach has also become notably costly, averaging $4.24 million.
Particularly concerning are the fines related to GDPR violations, which surged seven-fold in 2021, surpassing a billion dollars. These financial penalties are only part of the equation; organizations also suffer lasting damage to their reputation and trust from inadequate sensitive data protection.
Data anonymization is crucial for complying with privacy regulations like GDPR in Europe or HIPAA in the United States. It allows organizations to share and analyze data while minimizing the risk of exposing sensitive information about individuals. In this article, you will learn about data anonymization, its importance and advantages in ethical data analytics, and what techniques you can use to implement it.
Let’s explore!
Data anonymization
Data anonymization is the process of removing or encrypting personally identifiable information (PII) in a database so that the identity of the individual to whom the data belongs remains anonymous. It protects the private or sensitive data of an individual or a company by concealing it or preventing it from being re-identified.
Data anonymization aims to protect individuals’ privacy and confidentiality while still making the data useful for analysis, research, or other purposes. Various techniques are used to make data anonymous, such as generalization, suppression, data swapping, noise addition, and more.
Data anonymization allows information sharing within a single organization or between different organizations. For example, Cybernews recommends using a VPN for international travel when analysts need to access anonymized datasets securely across borders without exposing sensitive data to untrusted networks. For mobile professionals, setting up a VPN iOS app ensures the same level of encrypted access and privacy protection while working on the go. This same principle is key for travel fraud prevention, ensuring data remains safe even when accessed internationally. It accomplishes this by minimizing unintentional data exposure, making it possible to conduct evaluations and perform analytics after the data has been anonymized in specific settings. Data anonymization is crucial for complying with privacy regulations like GDPR (General Data Protection Regulation) in Europe or HIPAA (Health Insurance Portability and Accountability Act) in the United States.
Importance of data anonymization
The importance of data anonymization lies in its ability to balance the need for data utility with the imperative of protecting individual privacy.
Data anonymization protects individuals’ privacy rights by ensuring sensitive personal information cannot be linked back to specific individuals, reducing the risk of unauthorized access, identity theft, or other privacy breaches. Many data protection laws and regulations require organizations to protect the privacy of individuals’ data. Failure to comply with these regulations can result in severe penalties. Data anonymization is often a necessary step to meet these legal requirements.
Anonymized data can be shared more easily and widely, fostering collaboration between organizations and researchers. Such data sharing can lead to valuable insights, research, and innovations while mitigating the risks associated with sharing sensitive information.
Ethically, organizations are responsible for protecting the privacy of their customers, clients, and employees. Anonymization helps organizations demonstrate their commitment to ethical data-handling practices. Anonymization reduces the risk of data breaches and cyberattacks. Even if an attacker gains access to anonymized data, it should be much harder, reducing the potential harm.
Quick note: If you’re working with distributed teams, it’s also worth understanding the hidden data risks that can creep in through access, sharing, and everyday workflows.
Advantages of data anonymization
Data anonymization offers significant advantages by protecting customer trust, safeguarding against data misuse and insider threats, and enhancing governance and consistency in data handling. It is a critical practice for organizations looking to manage data while responsibly minimizing privacy and security risks.
1. Protects against the possible loss of market share and trust
Anonymization minimizes the risk of data breaches and leaks. In the event of a breach, the stolen data is less valuable since it’s anonymized and doesn’t contain personally identifiable information (PII). It reduces the potential harm and mitigates the loss of trust that could occur if sensitive information were exposed.
Data anonymization helps organizations protect the privacy of their customers’ sensitive information. Doing so demonstrates a commitment to safeguarding customer data, which is crucial for maintaining trust. When customers believe their data is handled responsibly, they are more likely to continue doing business with the organization.
2. Safeguards against data misuse and insider exploitation risks
Data anonymization not only protects against external threats but also safeguards against insider misuse of data, a key component of threat intelligence. Even employees or insiders with access to anonymized data are less likely to exploit it for personal gain or malicious purposes since the data cannot be easily linked back to specific individuals.
By anonymizing data, organizations reduce the temptation for employees or collaborators to access or misuse sensitive information inappropriately. It fosters a culture of responsible data handling within the organization and reduces the risk of legal and ethical violations.
3. Increases governance and consistency of results
Anonymization provides a structured and consistent method for handling data, ensuring that privacy protection is applied uniformly across the organization. It promotes good data governance practices and reduces the likelihood of ad-hoc, error-prone data handling. Data anonymization is often a requirement of data protection regulations like GDPR and HIPAA. By consistently applying anonymization techniques, organizations can demonstrate compliance with these laws, reducing the risk of costly legal consequences and fines.
When data is anonymized, irrelevant or unnecessary personal information is removed or generalized. It results in cleaner, more focused datasets for analysis, which, in turn, can improve the quality and reliability of analytical results.
Techniques of data anonymization
Achieving perfect anonymity can be challenging, and the effectiveness of anonymization techniques depends on various factors, including the nature of the data and potential external information sources. Some common methods include the following:
1. Generalization
In generalization, specific data values are replaced with broader, less precise categories or ranges. This approach decreases the level of detail in the data and reduces the more comprehensive picture of the patterns and insights it offers. Specific data points are intentionally omitted in the generalization process to reduce their identifiability. For instance, exact ages are replaced with age groups (e.g., 20-30, 30-40), or specific locations are replaced with regions (e.g., city names with states or countries).
2. Data Masking
Data masking replaces characters or digits with symbols or fake data. It’s often reversible for authorized users and used in scenarios like masking credit card numbers, social
security numbers, or email addresses in test or development environments.
3. Data Swapping
Data swapping involves exchanging certain attributes or records between individuals while keeping the overall dataset structure intact, making it difficult to link specific characteristics to individuals. It introduces alterations in the microdata set while preserving the detail and structure of the original data. It is often employed in scenarios where maintaining data relationships is important, such as surveys or demographic data.
4. Hashing
Hashing transforms data into fixed-length strings of characters (hashes). It’s a one-way process suitable for protecting passwords or other sensitive information. Organizations often implement comprehensive workforce password management systems that use hashing algorithms to securely store employee credentials while maintaining access control to anonymized datasets. The process is deterministic, meaning the same input data will always produce the same hash value. Its applications are found in cybersecurity and user authentication.
5. Pseudonymization
Pseudonymization involves replacing PII with pseudonyms or codes, making it more challenging to identify individuals. Unlike anonymization, pseudonymization allows for data re-identification with proper access controls. It is commonly used in healthcare (e.g., replacing patient names with unique identifiers) and research to protect individual identities while enabling data linkage for authorized users.
GDPR and data anonymization
Data anonymization is closely linked to the General Data Protection Regulation (GDPR), a comprehensive privacy law in the European Union. GDPR places strict requirements on how the personal data of individuals in the EU is handled and processed. While data anonymization is not explicitly defined in the GDPR, it is a key technique for achieving compliance.
GDPR defines “personal data” as any information that can directly or indirectly identify a natural person. Anonymized data, by definition, should not contain such identifiers, rendering it outside the scope of GDPR. Therefore, properly anonymized data is exempt from many GDPR requirements because it no longer qualifies as personal data. It is crucial for data sharing across borders. Data anonymization also extends to GDPR’s stipulations regarding data storage limitations, permitting organizations to retain anonymized data for extended periods, thereby enhancing their capacity to determine persistent trends and construct predictive models.
Other key considerations to achieve GDPR-compliant data anonymization include assessing the potential for re-identification to adjust anonymization techniques, avoiding over and under-data anonymization, preventing data linkability and unauthorized access, and maintaining documentation of data processing activities. Organizations must continuously monitor and review data anonymization processes to maintain GDPR compliance.
US privacy laws and data anonymization
The United States does not have a single-point, comprehensive federal privacy law similar to the European Union’s GDPR. Instead, U.S. privacy laws are a patchwork of sector-specific regulations and state-level laws. Therefore, the rules and guidance related to data anonymization can vary depending on the specific sector and state in which an organization operates. Generally, U.S. data protection laws presume that the de-identification process safeguards the privacy of data subjects. Below is a brief overview of US privacy laws concerning data anonymization:
- HIPAA (Health Insurance Portability and Accountability Act): HIPAA is a federal law containing provisions for de-identifying patient’s protected health information (PHI), a form of data anonymization. De-identified data is not subject to HIPAA regulations, but strict criteria must be met to consider data as de-identified. It establishes strict rules and requirements for the handling and sharing of PHI to ensure patient confidentiality. The best EMR for solo practice helps ensure compliance with regulations, offering secure management of patient data.
- California Consumer Privacy Act (CCPA): CCPA is a comprehensive data privacy law in the state of California, US. It enhances the privacy rights and data protection of California residents and gives California consumers the right to know, opt-out, and request the deletion of their personal information. Anonymization may be a method organizations use to fulfill deletion requests while retaining data for analysis.
- Other State-Level Privacy Laws: Several U.S. states have enacted or proposed their own privacy laws, which may include provisions related to data anonymization, breach notification, and consumer rights. These laws vary in scope and requirements.
Data anonymization tools
Data anonymization tools are software designed to assist organizations in the process of anonymizing or de-identifying sensitive data. They help organizations achieve data anonymization by applying various techniques and methods to protect individual privacy while retaining the utility of the data for analysis, research, or other purposes. You can automate and streamline the data anonymization process, making it more efficient and reliable.
Data anonymization tools typically offer the following features:
- They allow automatic identification of sensitive information (PII) within a dataset.
- They allow you to choose the appropriate anonymization technique based on the nature of the data and the desired level of anonymization.
- They allow you to transform sensitive data into a protected format and introduce randomness or noise into the data to make re-identification more challenging.
- They validate the anonymized data to ensure it complies with privacy regulations and security standards.
- They offer integration capabilities with other data management, analytics, or reporting tools.
- And more.
Data anonymization tools have user-friendly interfaces, can be scaled to handle large volumes of data, and offer customization. Below are some popular tools that provide data anonymization:
- ARX: ARX is an open-source data anonymization tool to anonymize sensitive personal data. It has an intuitive graphical user interface with cross-platform compatibility.
- Clover DX’s Data Anonymization Tool: Cover DX’s tool effectively transforms production-level data into anonymized datasets. You can choose the anonymization level of the resulting data.
- Docbyte’s Real-time Automated Anonymization: Docbyte’s tool uses AI and machine learning for anonymization. It anonymizes images and information in real-time as soon as they enter the system. This tool requires minimal human intervention to anonymize sensitive data once installed.
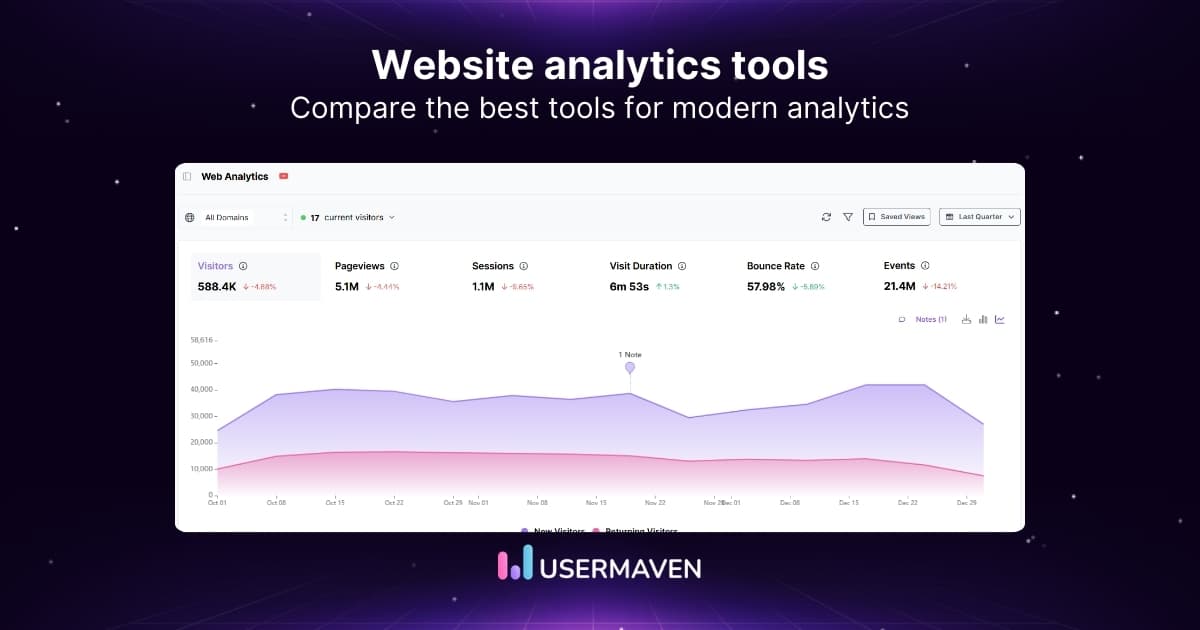
Data anonymization in Usermaven
Privacy-friendly data analytics is paramount to meet regulatory compliance. Website and product analytics tools like Usermaven, primarily designed for extracting insights and patterns from your website and product data, also offer data anonymization. Usermaven is easy to set up and use with quick no-code event tracking and a user-friendly interface. Due to its high usability, you don’t need developers and data scientists to track user activity across websites and products. Below is a detail on features of Usermaven that offer data anonymization.
1. Cookieless tracking
Most data analytics tools use cookies to collect user data, which raises concerns about respecting users’ privacy and compliance with privacy reg
ulations. The privacy and compliance aspects of these cookies depend on their responsible usage, which is subjective.
Usermaven takes a different approach with cookie-less tracking, offering an impressive 99% accuracy rate. This innovative method bypasses adblockers and the vulnerabilities associated with cookie-based tracking used by other tools. Usermaven’s cookie-less tracking prioritizes privacy by eliminating reliance on cookies, ensuring data accuracy, employing contextual targeting, and adhering to relevant data collection regulations.
2. GDPR & CCPA compliance
In the contemporary tech landscape, a heightened awareness of privacy issues has caused the emergence of regulations that protect users’ personal information and prevent potential misuse of their data. Thus, businesses are compelled to adhere to these privacy laws and regulations to avoid financial penalties and maintain their customer trust. Therefore, Usermaven is compliant with GDPR and CCPA.
3. User access controls and data governance
Usermaven includes access control mechanisms and data governance features. These data analytics tools enable organizations to restrict access to sensitive data and enforce data handling policies. Organizations can use access controls to limit who can access and analyze sensitive user data, reducing the risk of data exposure.
4. Data filtering and selection
Usermaven allows users to filter or select specific data attributes or records for analysis. By excluding or concealing sensitive information during the selection process, these tools indirectly contribute to data anonymization.
Data analysts can choose to work with subsets of data that do not contain personally identifiable information (PII) or sensitive details, reducing the risk of exposing such information during analysis.
It’s important to note that while data analytics tools offer some data anonymization capabilities, they are not a substitute for dedicated data anonymization solutions or processes. To ensure robust data anonymization and privacy protection, organizations should integrate data anonymization techniques and policies as a fundamental part of their data management strategy alongside analytics tools.
Conclusion
Data anonymization is a critical privacy technique that protects sensitive information while maintaining data utility. It involves various methods, such as generalization, suppression, pseudonymization, and noise addition, to transform data in a way that makes it difficult to re-identify individuals or entities.
Anonymized data is crucial for organizations that must share or analyze data for legitimate purposes while complying with data protection regulations like GDPR, HIPAA, or CCPA. It reduces the risk of privacy breaches and ensures that confidential information is not misused.
While data anonymization offers significant benefits, it also comes with challenges and limitations. These include potential loss of data utility, re-identification risks, complexity in implementation, and regulatory compliance challenges. The choice of anonymization techniques should align with specific use cases, data types, and regulatory requirements. Organizations must strike a balance between protecting individual privacy and maintaining the usefulness of data for analysis and decision-making. They should periodically review and update their anonymization practices to adapt to evolving privacy risks and regulations.
Grow smarter with privacy-first analytics
*No credit card required
FAQs
Which data anonymization techniques do I need?
The choice of data anonymization techniques you need depends on several factors, including your specific use case, the nature of the data you’re working with, and the privacy regulations that apply to your organization. Some common data anonymization techniques include generalization, pseudonymization, differential privacy, data swapping, and more.
Does data anonymization really hide your Identity?
In practice, achieving perfect data anonymity is exceptionally challenging, especially when dealing with rich and detailed datasets. The goal of data anonymization is not necessarily to guarantee absolute anonymity but to minimize the risk of re-identification to an acceptable and legally compliant level, given the context and use case.
Which kinds of data should be anonymized?
Data anonymization is typically applied to datasets that contain sensitive or personally identifiable information (PII). Some data types that need to be anonymized include healthcare data, financial data, geolocation data, HR & employee data, market research & customer data, legal data, online activity data, and information from health coaching software.
What are the disadvantages of data anonymization?
Some disadvantages and limitations are associated with data anonymization. Removal or alteration of data can result in loss of data utility for analysis and decision-making. Re-identification can compromise privacy and lead to data breaches, especially if the anonymized data is improperly handled. Anonymization techniques can introduce data quality issues, such as data distortion, inaccuracies, and loss of context.
What is the difference between data masking and data anonymization?
Data masking and anonymization are used for protecting data but have different objectives and methods. Data masking conceals or hides sensitive data so that it can still be used for certain purposes, such as testing, development, or user training. Data anonymization transforms or modifies sensitive data so that it becomes irreversibly anonymous, making it extremely difficult or impossible to re-identify individuals or entities.
Try for free
Grow your business faster with:
- AI-powered analytics & attribution
- No-code event tracking
- Privacy-friendly setup